During AIX installation default set of user accounts have been created, and the main purpose of these to prevent root from owning all filesystems and files. If these users and group IDs are not needed, you can remove them to minimize security risks associated with them. (Most typically uucp, nuucp, guest, lpd can be removed.)
root: superuser (UID 0), system administrators log into it to perform system maintenance and problem determination.
bin: owns important system dirs/files (so not only root owns all important files), and also owns the executable files for user commands
daemon: responsible for executing server processes, owning these processes and the associated files
sys: owns the default mounting point for the Distributed File Service (DFS) cache (I have not much info about DFS???)
adm: ownership of diagnostic tools
guest: useful to give access to the system for someone who has no account on the server
nobody: it is used by the Network File System (NFS), and to enable remote printing
uucp: (unix-to-unix copy) this user owns the files when transferring data between Unix servers over a dedicated line or telephone line
nuucp: uucp and nuucp, are created when bos.net.uucp fileset is installed. Logging in as uucp is not allowed, with nuucp it is possible
lpd, lp: used for starting the lpd daemon which is necessary to do remote printing.
invscout: used by Inventory Scout. This tool checks software and hardware configurations on the Hardware Management Console (HMC).
imnadm: it is used by the AIX Documentation Search Service to conduct searches of online HTML documents
USER INFORMATION:
/etc/passwd contains the basic attributes of users. (username, if pw set, uid, gid, GECOS, home dir, shell)
(* means invalid or password is not set, ! means user has a password)
/etc/security/passwd it contains the password (encrypted) and other information. (here is the ADMCHG flag...)
root:
password = D2ylo7rm3Qw7g
lastupdate = 1244118051
flags =
pw: encrypted pw, if pw contains only an asterisk (*), account is locked until a password has been set
lastupdate: number of seconds since epoch (1970. jan. 1) when the password was last updated
flags: restrictions to changing the user's password. You can set three different flags:
* ADMIN. If set, only the root user can change the user's password.
* ADMCHG. If set, the user is prompted to change his or her password on the next login/su.
* NOCHECK. If set, any additional restrictions in /etc/security/user are ignored.
/etc/security/user contains the most important settings, outside of the basics in /etc/passwd(umask, expires settings...)
uucp:
admin = true
login = false
rlogin = false
su = true
...
/usr/lib/security/mkuser.sys when new user is created (with mkuser) this script is executed
it will use the default parameters from file: /usr/lib/security/mkuser.default
creates home directory, sets permission, copies /etc/security/.profile as users profile
/etc/security/.profile this is the template .profile, which is copied when a new user created
(if you make changes in this file, the new users .profile will look like this file)
-----------------------------------
User profile is set up in the following way:
1. /etc/environment
PATH=/wherever:/right/there
2. /etc/profile which is shell script
PATH=$PATH:/somewhere/else
export PATH
3. users .profile
which is copied from /etc/security/profile at user creation
-----------------------------------
USER ULIMIT:
The /etc/security/limits file contains all the ulimits, or users' system resource limitations. The values are set with the mkuser command when the user is added to the system, or changed with the chuser command. A soft limit is a value that a user or application can change on the fly up to the maximum (the hard limit). The hard limit is just that -- the maximum value a parameter can be set to. (you can set the parameter to -1, which translates to unlimited. )
(in smitty user or chuser, you can set the hard and softlimits, e.g. chuser fsize_hard=4000000 bb)
The /etc/security/limits file contains a section called default that defines a template of standard values for each user unless that user has set custom values. It can be changed with "vi" or with command "chuser" or for temporary for that user sesion with command "ulimit".
With the ulimit command, you can change your soft limits, up to the maximum set by the hard limits and ulimit command affects the current shell environment.
change user's ulimit parameters:
su - bb "-c ulimit -a" <--shows user ulimit settings
chuser core=2000000 bb <--change user core file size
chuser rss=-1 rss_hard=-1 data=-1 data_hard=-1 <user> <--data and memory unlimited, rss:memory (shared memory), data: data stack
su - bb "-c ulimit -a" <--check new settings (or you can see in /etc/security/limits)
Max user process:
lsattr -EHl sys0 <--shows many things, maxuproc also
Normally there are three things we change for oracle. the system maxuproc and oracle's fsize and data segment size:
chdev -l sys0 -a maxuproc=512 <--reboot is needed only for decresing (F1 in smitty)
chuser fsize=-1 data=-1 oracle
-----------------------------------
SUID, SGID, SVTX
SUID Permission Bit:
An additional permission bit that can cause serious security problems is the SUID (set user ID). The SUID on an executable file means that when the file is executed, the process runs with an effective UID of the owner of the file. The SUID is not supported on shell scripts, and it has no meaning on a directory
SGID Permission Bit:
Another additional permission bit is the SGID (set group ID). The SGID on an executable file means that when the file is executed, the process runs with an effective GID of the group owner of the file. The SGID on a directory means that any file or directory created within the directory will have the same group ownership as the directory, rather than of the primary group of the user. The SGID permission bits are propagated down through the directory structure, so any directory created within a directory with the SGID bit set also inherits that bit
The SVTX Permission Bit:
The last of the additional permission bits is the SVTX, also referred to as the sticky bit. The SVTX on a directory means that even if the directory has global write permission (such as /tmp), users cannot delete a file in the directory unless they own the file or the directory
If the third bit is a lowercase s, it indicates that the SUID bit is set and that the execute permission (x) is turned on. An uppercase S indicates that the file has the SUID turned on but not the execute permission
Using Octal Notation
In octal notation, you are probably familiar with setting permissions, using three numbers such as 777 to indicate rwxrwxrwx. There is actually another position that is 0 by default, so 777 is really 0777. If you want to set the SUID, SGID, or SVTX permission bit, this position takes on a value other than 0. SUID is assigned a 4; SGID is assigned a 2, and SVTX is assigned a 1. Use the appropriate value to turn on that permission
root@aix1: /home/bubba # chmod 7777 bb01
root@aixi1: /home/bubba # ls -l | grep bb01
-rwsrwsrwt 1 root system 0 Jul 02 15:39 bb01
root@aix1: /home/bubba # chmod 7666 bb01
root@aix1: /home/bubba # ls -l | grep bb01
-rwSrwSrwT 1 root system 0 Jul 02 15:39 bb01
-----------------------------------
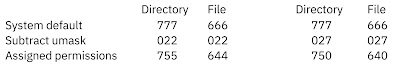
umask
umask determines the permissions for new files and directories (for example if files are created with 644 or 640 permissions). /etc/security user file contains the umask value, which is by default: 022. It can be changed for the whole system, or for a specific user.
The umask logic is similar to the file/dir permissions, just with umas we need to subtract the umask value from a specific number to know with which permission a new file/dir will be created:
# umask
0022
# touch new.file; mkdir new.dir
drwxr-xr-x 2 root system 256 Nov 02 18:11 new.dir
-rw-r--r-- 1 root system 0 Nov 02 18:11 new.file
# umask 027
# touch new027.file; mkdir new027.dir
drwxr-x--- 2 root system 256 Nov 02 18:13 new027.dir
-rw-r----- 1 root system 0 Nov 02 18:13 new027.file
-----------------------------------
GROUPS:
adm takes care of most monitoring functions, such as performance, cron, and accounting
audit conducts system audits
system configures the system and standard hardware and also performs software maintenance
printq system manages queuing. Typical commands include enable, disable, qadm, and qpri
security handles password and user account issues.
staff the default group assigned to all new users
GROUP INFORMATION:
/etc/group Contains the basic attributes of groups.
/etc/security/group Contains the extended attributes of groups.
-----------------------------------
USER ADMINISTRATION RELATED COMMANDS:
mkuser Creates a new user
passwd Creates or changes the password of a user
pwdadm Change other people's passwords and does not require the old password (-q:shows flag, -c:clears it)
echo <user>:<password> | chpasswd; pwdadm -c <user> <--root user can change other users passwords by standard input
chuser Changes user attributes (except password)
chuser groups=staff,uucp bb <--adds user "bb" to groups: staff, uucp
rmuser Removes a user and its attributes
chsec Changes security related stanzas
chsec -f /etc/security/lastlog -a unsuccessful_login_count=0 -s account_name <--reset unsuccessful login count
chsh Changes a user's login shell
login Initiates a user session
dtconfig Enables or disables the desktop autostart feature
umask shows the actual umask
umask 022 sets the umask to 022 (umask of 000 would give 666 permissions on a file or 777 on a directory)
w who logged in
whoami who am i
who am i who am i with more details
last who logged in last to the system
finger username info about the user
lsuser -f <username> deatiled info about the user (-f: readable format)
rmuser -p <username> removes a user
(-p: removes auth. info from /etc/security/* files, the user's home dir is not removed automatically)
mkgroup makes a group
chgroup changes a group
lsgroup ALL lists all group
lsgroup -f <groupname> deatiled info about the user (-f: readable format)
rmgroup <groupname> removes a group from the system
pwdck verifies consistency between /etc/passwd, /etc/security/user, and /etc/security/passwd
usrck verifies consistency between /etc/passwd, /etc/security/user, and /etc/security/limits
grpck verifies consistency between /etc/passwd, /etc/security/user, /etc/group, and /etc/security/group
-n reports errors but does not fix them
-t reports errors and asks if they should be fixed
------------------------------------
User creation
1. smitty user
2. pwdadm username <--setting the password
3. pwdadm -c username <--removing the ADMCHG flag from /etc/security/passwd file
chuser unsuccessful_login_count=0 <user> clears unsuccessful login count
------------------------------------
nofiles ( number of file descriptors a process may have):
It specifies the number of open files permitted. If this value is set too low, a memory allocation error will occur on AIX and a too many files open will be logged to the to the stderr log file. Set this value higher than the default system value. For large multi-processor machines, set to unlimited.
# ulimit -a <--to query
# ulimit -n <new_value> <--to set to a new value
# ulimit -n -1 <--to set it to unlimited
------------------------------------
maximum number of processes per user:
'maxuproc' defines the max number of processes each AIX user can 'fork'. If it is set too low, you may not be able to create high number of database agents necessary to handle connections from your application. So it is recommended to set this to at least 4096.
To query current setting:
# lsattr -El sys0 -a maxuproc
To set to a different value:
# chdev -l sys0 -a maxuproc='4096'
------------------------------------
Copying users between AIX systems:
0. On source system check file consistency:
# usrck -t ALL
# pwdck -t ALL
# grpck -t ALL
1. These files should be copied:
/etc/group
/etc/passwd
/etc/security/group
/etc/security/limits
/etc/security/passwd
/etc/security/.ids
/etc/security/environ
/etc/security/.profile
These can be copied as well (between same AIX versions):
/etc/security/login.cfg
/etc/security/user
2. If needed edit /etc/passwd, to look like this:
root:!:0:0::/:/usr/bin/ksh
3. On destination system check file consistency:
# usrck -t ALL
# pwdck -t ALL
# grpck -t ALL
------------------------------------
Mass user creation:
32 users had to be created.
1. I created 3 files:
test1: contained usernames
test2: contained gecos fields of the users (in the same order as the users were in test1)
test3: contained home dirs of the users (same order as in test1)
(It could be done in 1 file, with 3 columns and awk the columns, but this way was easier for me)
2. This script was created:
x=1
while [[ $x -lt 33 ]]
do
i=`cat test1 | head -n $x | tail -1`
j=`cat test2 | head -n $x | tail -1`
k=`cat test3 | head -n $x | tail -1`
mkuser -a gecos="$j" home="$k" $i
(( x += 1 ))
done
3. After users were created, some attibutes were set to these users:
for i in `cat test1`; do chuser rlogin=true minage=0 maxage=0 maxexpired=-1 minalpha=0 minother=0 mindiff=0 maxrepeats=8 minlen=0 $i; done
4. User passwords have been set this way:
for i in `cat test1`; do echo $i:abcd1234| chpasswd; pwdadm -c $i; done
------------------------------------



20 comments:
How can I format the output of localtime? =
perl -le 'print scalar localtime 1223451491'
Please check this link:
http://www.perlmonks.org/?node_id=16212
I have an AIX script that copies files for a backup before over-writing data files that are being replaced. I have one customer that returns "multicp not found". I have tried several diff permissions and still not found. I tried recreating the file on the system and have the same problem. Just one customer, one box?
From your description it looks like multicp is the name of your script. From the error message it seems to be your shell can't find your script under that location. So, I think you should add to your PATH variable (in your profile or environment file) that directory where your script exists, or make sure your script exists uner that location where something is referring to it.
Hi How can I migrate and copy the /home, users, passwords and groups from one aix server to another. The second aix server is a brand new aix.
Thanks for your help.
Regards
Paul.
Hi, IBM published this documentation: http://www-01.ibm.com/support/docview.wss?uid=isg3T1000231
I would follow that, but to make sure please google, some forums are also dicussed this topic.
(I'll do some tests and after that I will publish it on this blog.)
Hi. I have checked that document but this document does not have information about how to migrate /home an folders inside /home.
I'm going to try the following scripts. Please your comments:
URL: http://www.tek-tips.com/viewthread.cfm?qid=1587110
If you're moving to a brand new system with no users created yet you can simply move the following files to the new box from the old box (please create backup files at the destination before the copy):
/etc/passwd
/etc/group
/etc/security/passwd
/etc/security/group
Then backup their home directories and restore them at the new box.
Using SSH it can be this easy:
Code:
tar cvf - /home/user1 | ssh newserver " ( cd /home/user1 ; tar xvf - ) "
Another thing to do once you have moved the files over is run the following commands to clear up any discrepancies:
usrck -t ALL
pwdck -t ALL
grpck -t ALL
Hi, that script looks OK :)
I did a test with 1 user and it worked for me, BUT there are few notes:
1. When you do the copy, the tar command contains "...cd /home/user1", but that directory does not exist at that moment. It is not a problem, because that command will create the mentioned directory. I just noted here, that not be surprised, when you see some outputs, that direcory not found.
2. After I copied the above mentioned files and the user home dir, on the new server I could not do "su - user1 ". This happened because /etc/security/user file was different on the servers:
old server:
default:
admin = false
login = true
su = true <--
new server:
default:
admin = false
login = true
su = false <--
After I updated this file on the new server I could do "su - user1 " with the user password, so everything was OK.
I just mentioned this because usually this method is workable, but if you have specific user settings, then other files should be checked or copied as well. (/etc/security/limits, /etc/security/environ, /etc/security/user)
please provide me the syntax to create a user with name,home dir, passwd,f size,passwd expiry etc
Hi....
If you hit mkuser commad what are the files will get updated...
Hi, those which are mentioned in the "Copying users betwwen AIX systems"
Hi admin..
I have recently faced a question in an interview.
What is the maximum no of users i can create in AIX.
Thank you...
Mar 4 02:05:44 aaaa daemon:err|error ftpd[16515082]: failed to write /var/adm/wtmp File too large
Mar 4 02:05:44 aaaa daemon:err|error ftpd[16515082]: failed to write /var/adm/wtmp File too large
Mar 4 02:05:45 aaaa daemon:err|error ftpd[16515084]: failed to write /var/adm/wtmp File too large
Mar 4 02:05:45 aaaa daemon:err|error ftpd[16515084]: failed to write /var/adm/wtmp File too large
Mar 4 02:05:47 aaaa daemon:err|error ftpd[53674066]: failed to write /var/adm/wtmp File too large
getting the above and wtmp file size is 2GB, will it affect ftp process?
Hi , I am unable to create test user in one of the AIX machine and getting error [ 91 Error changing "groups" ]
how we can trouble shoot this one ?
bash-4.2# mkuser test
3004-63004-691 Error changing "groups"
bash-4.2# oslevel -s
6100-01-09-1015
bash-4.2# cat /usr/lib/security/mkuser.default
user:
pgrp = staff
groups = staff
shell = /usr/bin/ksh
home = /home/$USER
admin:
pgrp = system
groups = system
shell = /usr/bin/ksh
home = /home/$USER
bash-4.2# cat /usr/lib/security/mkuser.sys
#!/bin/ksh
# IBM_PROLOG_BEGIN_TAG
# This is an automatically generated prolog.
#
# bos61V src/bos/usr/lib/security/mkuser.sys.sh 1.12.3.1
#
# Licensed Materials - Property of IBM
#
# COPYRIGHT International Business Machines Corp. 1989,1993
# All Rights Reserved
#
# US Government Users Restricted Rights - Use, duplication or
# disclosure restricted by GSA ADP Schedule Contract with IBM Corp.
#
# IBM_PROLOG_END_TAG
# @(#)18 1.12.3.1 src/bos/usr/lib/security/mkuser.sys.sh, cmdsuser, bos61V, 1209A_61V 2/22/12 10:43:05
#
# COMPONENT_NAME: CMDSUSER
#
# FUNCTIONS:
#
# ORIGINS: 27
#
#
# (C) COPYRIGHT International Business Machines Corp. 1989,1993
# All Rights Reserved
# Licensed Materials - Property of IBM
# US Government Users Restricted Rights - Use, duplication or
# disclosure restricted by GSA ADP Schedule Contract with IBM Corp.
#
#
# This file is no longer user customizable. To have a customized mkuser.sys script
# create a file /etc/security/mkuser.sys.custom and the /etc/security/mkuser.sys
# will run this script instead of the original mkuser.sys script.
export PATH=/usr/bin:/usr/sbin:$PATH
#
# Check the number of arguments first
#
if [ $# -ne 4 ]
then
exit 1
fi
#
# If a customer mkuser.sys.custom script exists
# then execute it instead and exit passing all arguments
# and returning the return code from mkuser.sys.custom
#
if [ -x /etc/security/mkuser.sys.custom ]
then
/etc/security/mkuser.sys.custom $*
exit $?
fi
#
# Create the named directory if it does not already exist
# and set the file ownership and permission
#
if [ ! -d $1 ]
then
last=$1
while [ 1 ]
do
dir=`dirname $last`
if [ -d $last ]
then
break
elif [ -d $dir ]
then
mkdir -p $1
chown -R bin:bin $last
chmod -R 700 $last
break
else
last=$dir
fi
done
chgrp "$3" $1
chown $2 $1
fi
#
# Copy the user's default .profile if it does not already
# exist and change the file ownership, etc.
#
if [ `basename $4` != "csh" ] && [ ! -f $1/.profile ]
then
cp /etc/security/.profile $1/.profile
chmod u+rwx,go-w $1/.profile
chgrp "$3" $1/.profile
chown $2 $1/.profile
else
if [ `basename $4` = "csh" ] && [ ! -f $1/.login ]
then
echo "#!/bin/csh" > "$1"/.login
echo "set path = ( /usr/bin /etc /usr/sbin /usr/ucb \$HOME/bin /usr/bin/X11 /sbin . )" >> "$1"/.login
echo "setenv MAIL \"/var/spool/mail/\$LOGNAME\"" >> "$1"/.login
echo "setenv MAILMSG \"[YOU HAVE NEW MAIL]\"" >> "$1"/.login
echo "if ( -f \"\$MAIL\" && ! -z \"\$MAIL\") then" >> "$1"/.login
echo " echo \"\$MAILMSG\"" >> "$1"/.login
echo "endif" >> "$1"/.login
chmod u+rwx,go-w $1/.login
chgrp "$3" $1/.login
chown $2 $1/.login
fi
fi
bash-4.2#
Hi,
How can i see who all users where logged into the AIX server at a particular time? I mean the logged in history of the server for last 1 month.
HISTTIMEFORMAT="%d/%m/%y %T "
Then
history
perl -e "print scalar localtime(1223451491)"
chuser gecos=vio administrator padmin
Usage: chuser [-R load_module] "attr=value" ... user
in aix 6.1, can any one help on this issue.
chuser "gecos=vio administrator" padmin will work
Hello ,
I need help in creating autoreset failed attempt script for user dbas. that I can place in cron.
Post a Comment