Passwords are stored cryptographically. When a user types in a password, it will go through a hashing algorithm and the end result is a cryptographic hash.
A hash is a cryptography term for a one-way function. A hashing algorithm provides a one-way transformation between clear-text and the encrypted-text, in this case, the hash. Hashes are “one way” because the encrypted string of characters cannot be directly decrypted, which means I cannot take my hash and get the clear-text again by running it through the hashing algorithm.
The other advantage of hashing, that an unfixed amount of input through a hashing algorithm produces a fixed amount of output. So, it doesn't matter how long the input is (100 characters or just one word) the end result (output/hash) always will be the same length.
(If they all have the same size, it becomes unfeasible to determine the type or length of the input given.)
A few popular hashing algorithms are MD5, SHA-1, SHA-2.
When a new user is created and a password is set, passwd program runs the entered string through a hashing algorithm. The hash is then added to the /etc/security/passwd file. By default the "old" crypt() programming function is used to generate the password.
Each time the user logs into the system and types in the password, AIX will compute the hash for the password and compares to the one stored in /etc/security/passwd file. If they match, the user will be allowed to login.
---------------------------------
/etc/passwd
# cat /etc/passwd
root:!:0:0:gecos:/home/root:/usr/bin/ksh
daemon:!:1:1:gecos:/etc:
bin:!:2:2:gecos:/bin:
sys:!:3:3:gecos:/usr/sys:
It contains the basic attributes of users. (username, if pw set, uid, gid, GECOS, home dir, shell)
(* means invalid or password is not set, ! means user has a password)
---------------------------------
/etc/security/passwd
It contains the passwords (encrypted) and other information (ADMCHG flag...) of users.
# cat /etc/security/passwd
root:
password = WBs4CK8E5a7VA
lastupdate = 1407504004
daemon:
password = *
user1:
password =
user2:
password = ub9CBz/bLn9zI
lastupdate = 1374196455
flags = ADMCHG
password: it is usually the encrypted pw,
if pw contains only an asterisk (*), account is locked until a password has been set (with ssh key you can login)
if it is empty (user1), this allows anyone to log in or “su” to that account without being prompted for a password
lastupdate: number of seconds since epoch (1970. jan. 1) when the password was last updated
flags: restrictions to changing the user's password. You can set three different flags:
ADMIN. If set, only the root user can change the user's password.
ADMCHG. If set, the user is prompted to change his or her password on the next login/su.
NOCHECK. If set, any additional restrictions in /etc/security/user are ignored.
It is possible to take the password hash of a user on one server and copy it to another server, so the user can log into the new server with the same password.
---------------------------------
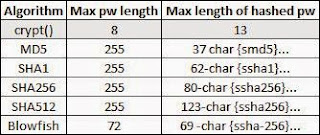
Password Encryption Algorithms
AIX 5.2 and 5.3 uses the old unix style crypt() function which has an 8 character limit. (It is possible to enter more than 8 characters, just it is looking at the first eight characters and ignoring everything else.)
AIX 5.3 TL7 and AIX 6.1 introduce Loadable Password Algorithm (LPA). Each supported password encryption algorithm is implemented as an LPA module that is loaded at runtime when the algorithm is needed. The supported LPAs, and its attributes, are defined in the /etc/security/pwdalg.cfg file.
The available Loadable Password Alogrithms (LPA) are listed in /etc/security/pwdalg.cfg:
There is a stanza for each module in the file:
ssha1:
lpa_module = /usr/lib/security/ssha
lpa_options = algorithm=sha1
ssha256:
lpa_module = /usr/lib/security/ssha
lpa_options = algorithm=sha256
To change the password hash algorithm, the following command syntax can be used. In this example SHA512 has been used:
chsec -f /etc/security/login.cfg -s usw -a pwd_algorithm=ssha512
(It can be done with vi as well.)
After changing it the previously generated password hashes will stay the same and continue to work. Users will be able to login to the system with those passwords. The new algorithm will be used the next time a user changes his/her password and then the password hash of the user in /etc/security/passwd will be updated to the new one. Until then they will continue to use their original password and hashing algorithm.
---------------------------------
/etc/security/login.cfg
This file will show the password hashing algorithm, which is in use globally on the system.
A valid value for pwd_algorithm is a name of stanza that is defined in /etc/security/pwdalg.cfg
shells = /bin/sh,/bin/bsh,/bin/csh,/bin/ksh,/bin/tsh,/bin/ksh93
maxlogins = 32767
logintimeout = 60
maxroles = 8
auth_type = STD_AUTH
pwd_algorithm = ssha512
If pwd_algorithm entry is missing here, the default value is "crypt" which is the legacy crypt() function.
---------------------------------
chpasswd changes password of users (-c will clear all password flags)
pwdadm administers users password (-c will clear all password flags)
echo "<user>:<pasword>" | chpasswd -c it changes a user password (good for scripting, but pw is in clear text)
(“-c” clears out the ADMCHG flag, at next login no pw change is needed)
Changing a user pw in script (avoiding clear text):
1. openssl passwd it will prompt for the password twice, then show the password hash
2. echo “root:Ywa8SDcGhSnHB” | chpasswd -ec it will change pw to the hash (-e encrypted format)
---------------------------------
Recovering root password:
1. Network boot from NIM (nim -o maint_boot -a spot ..., SMS network boot)
2. Choose: Access this volume group and start a shell
3. Run "passwd" from command prompt
4. Reboot to normal mode: sync;sync;sync;reboot
---------------------------------
6 comments:
Hi Balaz,
I have a doubt, we all are aware that a non-root user will not have write access to "/etc/passwd" file. But when a non-root user changes his/her own password using a "passwd" command, even the /etc/passwd file is encrypted by the new password. May I know how is this possible to change the /etc/passwd file for him/her while they still don't have access to it?
Hello,
passwords are stored in /etc/security/passwd. IBM writes this regarding accessing /etc/security/passwd:
"Access to this file should be through the system commands and subroutines defined for this purpose. Other accesses may not be supported in future releases."
Thanks a bunch for your reply :). I got the answer.
Its because, the path "/bin/usr/passwd" of passwd command is set with sticky bit.
Due to which whenever the command passwd is run by any user(root and non-root) they will be considered as a owner of the file but not as a user.
Upon setting what permissions even a root user will not be able to delete a particular file/folder.
Thanks in advance
It's change attribute(chattr)
chattr +i filname (to enable)
chattr -i filename(to disable)
Hello,
is there a way to change the password via commandline when ssha512 is used?
Using "openssl passwd -6" seems to be incompatible ...
Cheers,
ku
Post a Comment